How to Get a Job as an Ethical Hacker
If there was ever a time to get into the IT security field, it’s now: The Bureau of Labor Statistics expects the sector to grow 18 percent by 2024, and according to a survey by the Ponemon Institute, demand for talent so outweighs supply that 40 percent of IT security positions are expected to go unfulfilled in 2014. The pay isn’t bad, either: the average information security analyst in the U.S. makes over $96,040 per year.
One of the most in-demand positions in this field is that of an ethical hacker—an IT professional who purposefully penetrates networks and systems to find and fix potential vulnerabilities. If you’re looking to put on your “white hat” and infiltrate systems for good, this position can be a great career opportunity. Depending on your experience and skills, you can earn over $100,000 per year.
To help job seekers learn what’s involved in becoming an ethical hacker and the responsibilities of the position, we spoke with IT security professionals, instructors and certified hackers themselves. Here, we highlight the skills and certifications needed to rise to the top of the talent pool.
What Is an Ethical Hacker?
Ethical hackers are responsible for examining internal servers and systems to discover any possible vulnerabilities to external cyber attacks. Common job functions include conducting “pentests” (purposeful penetration tests to discover security weaknesses in a system) by using software applications such as Metasploit and BackBox Linux.
According to Damon Petraglia, director of forensic and information security services at Chartstone Consulting, other ethical hacker responsibilities include:
Providing recommendations on how to mitigate vulnerabilities;
Working with developers to advise on security needs and requirements;
Updating security policies and procedures; and,
Providing training as part of a company’s security awareness and training program.
What Are the Job Requirements?
A typical entry-level ethical hacker job posting reveals that a bachelor’s degree in computer science or a related work field is a must. Beyond that, security certifications can be extremely beneficial in proving you have the requisite knowledge for the job. One survey found that 81 percent of security professionals believe getting certified was a key factor in the decision to hire them.
While many IT security certifications exist, the three main ones for ethical hackers are:
Certified Ethical Hacker (CEH)
GIAC (Global Information Assurance Certification) Penetration Tester (GPEN)
Offensive Security Certified Professional (OSCP)
CEH: The Most Basic and Widely Recognized Certification
If you’re looking to get started as an ethical hacker, the CEH certification, the broadest of the three, may be right for you. Offered by the EC-Council, the CEH certification is designed to give IT security professionals a baseline knowledge of security threats, risks and countermeasures through lectures and hands-on labs.
According to Paul Coggin, a certified EC-Council instructor, it’s recommended that students who enroll in the course have a background in “Windows and Linux systems administration skills, and are familiar with TCP/IP [the core Internet protocol] and virtualization [creating a virtual version of a hardware or software platform].”
If you plan on skipping the classes and taking the exam without training, you’ll need to submit proof that you have at least two years of experience in IT security.
A big benefit with the CEH certification is flexibility: there are options for self-study, video lectures you can watch at your own pace and instructor-led lessons you can take online. The EC-Council even provides the option of bringing training to your business or organization. Upgrades for physical courseware, additional practice exams and tablet usage are also available.
Instructor-led lessons take place from 9 a.m. to 5 p.m. over the course of five days, and students can access online labs for up to six months. The latest version of the test consists of 125 multiple-choice questions. Students have four hours to complete the exam and must receive a score of at least 70 percent to receive the certification.
The cost of the CEH depends on the level of instruction needed: it ranges from $825 for the basic self-study coursework all the way up to $2,895 for instructor-led courses, online lab access, a test voucher and a test prep program. If you don’t buy the voucher, the test itself costs $500, and all students must pay a $100 application fee.
What You’ll Learn
The CEH certification provides the most general knowledge of the three highlighted here. “It’s not focused on a specific software product, technology or skill domain,” Coggin explains. “It provides a broad survey of various domains in computer security.”
To this end, the course covers everything from how to scan networks and identify basic viruses to hijacking web servers and penetration testing.
According to James Conrad, a 20-year IT security professional who teaches a video series for CBT Nuggets on the CEH certification, students will also learn how to “crack passwords, use steganography [hiding information to get it through security measures], create remote access trojans, perform denial of service (DoS) attacks and hack wireless networks, among many other skills.”
Another big focus of the course is understanding social engineering, or the process of manipulating individuals to gain personal information or infiltrate computer systems. In today’s world, where social media has led to growing interactions between humans and technology, Conrad says social engineering is a vital skill to learn in order to stay ahead of potential threats.
According to Brian Brock, chief information officer at Nivsys who became CEH certified last year, the course also includes a heavy focus on the RAPID7 suite of tools (one of which is the aforementioned Metasploit), which enable ethical hackers to complete comprehensive pentests, from initial scanning to final analysis and planning.
The Benefits
The greatest value the CEH certification holds is being able to put it on your resume. When it comes to getting a job as an ethical hacker, “CEH is the original standard,” says Albert Whale, president and chief security officer at IT Security, Inc. Petraglia agrees, and says it’s “probably the best recognized” of the three certifications.
According to PayScale, median pay for CEH-certified professionals is as follows:
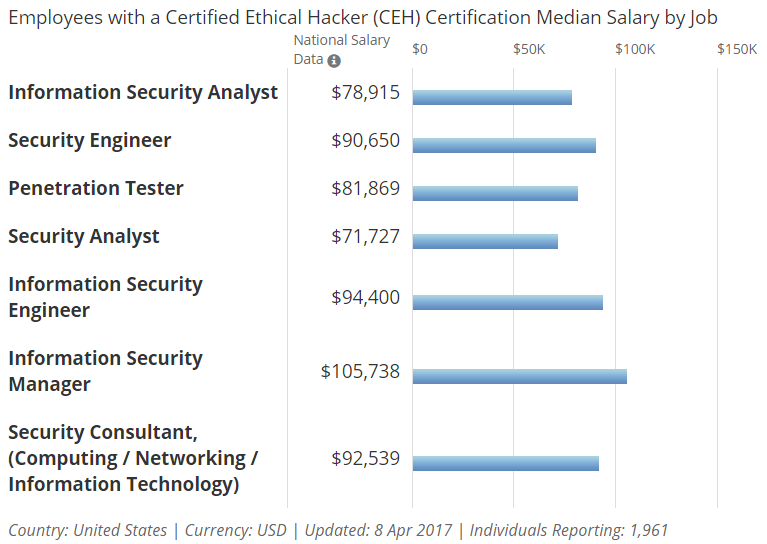
However, as some bloggers have noted, the certification has its caveats. The course is heavy on text and video instruction, without a lot of hands-on practice. Another complaint is that material is outdated and too simple to be useful for day-to-day use.
“The certification is great to have, and it looks amazing on a resume,” says Christian Crank, a security researcher at TrainACE who took the course five months ago. “But the book that’s used is poorly assembled: it’s essentially a collection of PowerPoint slides and doesn’t elaborate on what needs to be taught.”
Homer Minnick, director of the Cybersecurity Academy at UMBC Training Centers agrees, saying that most CEH courses “don’t provide an adequate amount of hands-on application.”
Summary: If you’re looking to break into the field of ethical hacking, the CEH certification offers a great opportunity to get ahead of other applicants, but don’t expect to learn everything you need to know from the course materials alone.
GPEN: A More Comprehensive, yet Costly Certification
For those looking to learn the complete ins and outs of being an ethical hacker, there’s the SEC560 course on Network Penetration Testing and Ethical Hacking from the SANS Institute, which many people enroll in prior to taking the GPEN certification test. As author and lead instructor of the course Ed Skoudis explains, SEC560 is “a comprehensive course on penetration testing—end to end.”
While the SEC560 course is recommended, it’s not required to take the test for GPEN certification. There are no steadfast prerequisites, but it’s recommended that students have a basic understanding of different types of cryptography (transforming information to keep it secure), Windows, Linux and TCP/IP. Should you need it, there are also optional “refresher” tutorials available on the first day of class.
You can take the SEC560 course in-person or online through live training or on-demand lessons. Whatever path you choose, it’s not cheap: online training is $5,095, but includes access to the online labs. In-person training, on the other hand, is $4,695, but you’ll need to pay an extra $599 to get access to the online labs.
Regardless of which route you take, you’ll also have to spend $599 to take the GPEN certification test. Should you choose to skip the course and go straight for certification, the cost of the test rises to $1,049.
The open book exam consists of 115 multiple choice questions. You must complete it within three hours and score at least a 74 percent to receive certification.
What You’ll Learn
Through over 30 labs (and a final, team-based “capture the flag” event), students will get hands-on experience in every facet of pentesting, from detailed reconnaissance and scanning to writing a perfect penetration testing report from a management and technical perspective.
“The focus of the class is to learn how to do penetration tests that have high business value,” Skoudis explains. “We teach technical excellence so it has real business impact. The goal is to get you ready to do a comprehensive pentest.”
Coursework is completed through a Linux distribution that every student receives, which contains Metasploit tools along with free open-source software, such as the password-breaker John the Ripper. According to Skoudis, the course only uses “the most widely-used and best tools available.”
The SEC560 course also teaches IT professionals how to look at business platforms from the mindset of a hacker. “The class tries to change your mindset so you don’t think of functionality as it was intended,” says Vice President of Information Security for Bessemer Trust Vikas Bangia, who became GPEN-certified last year. “Instead, you focus on possible programming and functionality flaws that allow you to do things the software was not meant to do.”
The Benefits
The high cost is a formidable barrier, but the SEC560 course provides a nice balance between theory and hands-on practical application, and does a good job developing the “soft skills” necessary to thrive as an ethical hacker in the business world.
“SANS training is awesome,” Bangia says. “The instructors are the top people in the field and know technology better than anyone in the world.”
The GPEN certification can also provide a significant career boost. Bangia says he received a raise after getting certified, and according to Foote Partners’ IT Skills & Certifications Pay Index for Q1 2014, the GPEN certification was one of four GIAC certifications to gain 10 percent or more in market value over the previous quarter.
If you do decide to take the SEC560 course, be prepared to work hard. Bangia warns that there’s a huge amount of information that you have to absorb over the six days of the course, but notes that there is “ample opportunity” to ask questions.
Summary: The GPEN certification offers a lot of material and hands-on practice to give you the know-how to become an ethical hacker, but it may be impractical for those who can’t afford the $5000+ price tag.
OSCP: The Lesser-Known, More Technical Certification
Claiming to be the world’s first completely hands-on offensive information security certification, the OSCP certification is not for those looking for a classroom setting. According to Offensive Security, which administers the certification, the goal of the OSCP is “for students to prove they have a clear, practical understanding of the penetration testing process and lifecycle.”
Before you become OSCP-certified, you must complete the Penetration Testing with Kali Linux (PWK) course, which is based around the Kali Linux Distribution, an open source project maintained by Offensive Security. According to the course website, “a solid understanding of TCP/IP, networking and reasonable Linux skills are required.”
You’ll most likely be taking this course online, as live training is only available in Las Vegas. The price you pay depends on how long you want access to the online labs: it ranges from $800 for 30 days up to $1150 for 90 days. This price includes online video lessons, access to the labs and the certification test. You can also purchase additional lab access time if you need it.
An important thing to note is that the OSCP certification bucks the trend of a normal multiple-choice test. Instead, you’re given a virtual network with varying configurations and are tasked with researching the network and identifying vulnerabilities and hacking in order to gain administrative access. You must also detail your findings in a comprehensive penetration test report, just like you would do while on the job.
You’re given 24 hours to do the test, and your report is reviewed by a certification committee to determine whether or not you’ve passed.
What You’ll Learn
In addition to learning about pentesting tools and techniques, the OSCP also emphasizes efficiency and taking a creative approach to solving problems.
“Most importantly, you learn methodologies and how to think laterally,” says Ken Westin, security analyst at Tripwire, who became OSCP-certified last year.
“It’s one thing to successfully exploit a vulnerability, but then you learn how to escalate privileges [exploit bugs to gain unauthorized access] and use that as a stepping stone to the next objective. You learn how to automate a great deal of tasks, sift through large amounts of data and identify targets using scripts you write yourself.”
The Benefits
Be forewarned: the OSCP isn’t for the faint of heart. The hands-on approach takes a lot of time and trial and error—but this can extremely beneficial in the long run.
“I think the best part of the course is that it’s completely hands-on,” Westin says. “Offensive security needs to be learned in an actual, legal environment, where you’re hands-on with the tools in real scenarios.”
However, not having a live instructor to ask questions can be frustrating. “It would have been nice to have an instructor assist in the labs to help save me some time,” Westin says.
The certification also isn’t as well-known as the CEH Certification, so don’t expect an initial boost over other applicants in the field. “I see a benefit from the education I received, but not necessarily from the certification itself, as most people don’t know what it is,” Westin says.
According to PayScale, median pay for professionals with OSCP Certification is as follows:

The hands-on modules and training coupled with the OSCP’s unique simulation exam provides real world experience that other certifications may lack.
“To get a concealed carry permit, you don’t need to prove you know how to use a gun,” Westin says. “You just pay your fee, get fingerprinted and some learn some basic safety principles. But hands-on certifications like the OSCP are more involved, where you need to not only know how the gun works, you also need to be able to put it together, pass accuracy tests and demonstrate your ability to use it in real life scenarios.”
Summary: While it won’t get as much name recognition, the hands-on skills the OSCP certification teaches are invaluable to an ethical hacker position. Be prepared for challenging coursework you may not receive much assistance with.
Which Certification Should I Get?
| CEH | GPEN | OSCP |
Cost | $1500 – 2695 | $5,910 | $800 – 1150 |
Time (on-site) | 5 days | 6 days | Optional 30, 60, and 90 days based on price |
How to take it | On-site, self-study, online video lessons, online instructed lessons | On-site, online video lessons, online instructed lessons | On-site, online video lessons |
Software taught | RAPID7 | Metasploit, free open-source tools | Kali Linux Distribution |
Pros | Flexible course options, widely recognized | Teaches soft skills, excellent instructors | Low cost, hands-on exercises and exam |
Cons | Outdated information, lack of hands-on exercises | High cost, shorter access to materials | Lack of live instruction, not as recognized |
At the end of the day, these certifications are merely a supplement to real-world experience—not an alternative. Even then, having a wealth of security knowledge and a passion for the industry can only get you so far.
“Inside an enterprise, it’s not all about breaking systems and applications,” explains Adam Ely, former COO and co-founder of Bluebox Security (acquired by Lookout in 2016) and former CISO at Salesforce.com. “It’s also about thinking how to best protect the company and customers when a problem is found, and thinking about how to do it with real world constraints.”
“I look for someone who looks at hacking from a human perspective,” Petraglia adds. “Many times, social engineering is combined with technical hacking activities to execute an attack. It’s important that the ethical hacker understands the complex interrelations between humans, machines, threats and vulnerabilities.”